受到xmlrpc.php拒绝服务攻击
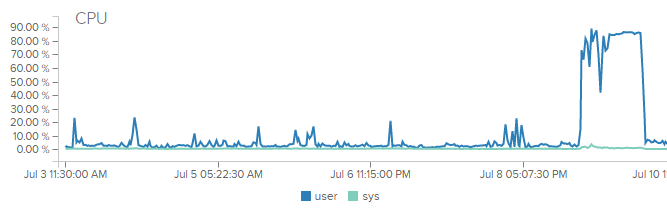
昨天发现博客开始出现502和504错误,最开始以为是php5-fpm 有什么bug,因为重启一下php5-fpm 就好了。但是后来重启都没有用了,于是分析了一下,发现受到了攻击。
被攻击后CPU占用一直100%,是几个php5-fpm 进程。
2015/07/10 08:44:19 [error] 2858#0: *13803 connect() to unix:/var/run/php5-fpm.sock failed (11: Resource temporarily unavailable) while connecting to upstream, client: 185.62.189.239, server: jayxon.com, request: "POST /xmlrpc.php HTTP/1.0", upstream: "fastcgi://unix:/var/run/php5-fpm.sock:", host: "jayxon.com" 2015/07/10 08:44:19 [error] 2858#0: *13805 connect() to unix:/var/run/php5-fpm.sock failed (11: Resource temporarily unavailable) while connecting to upstream, client: 188.209.52.133, server: jayxon.com, request: "POST /xmlrpc.php HTTP/1.0", upstream: "fastcgi://unix:/var/run/php5-fpm.sock:", host: "jayxon.com" 2015/07/10 08:44:19 [error] 2858#0: *13807 connect() to unix:/var/run/php5-fpm.sock failed (11: Resource temporarily unavailable) while connecting to upstream, client: 188.209.52.133, server: jayxon.com, request: "POST /xmlrpc.php HTTP/1.0", upstream: "fastcgi://unix:/var/run/php5-fpm.sock:", host: "jayxon.com" 2015/07/10 08:44:19 [error] 2858#0: *13809 connect() to unix:/var/run/php5-fpm.sock failed (11: Resource temporarily unavailable) while connecting to upstream, client: 188.209.52.133, server: jayxon.com, request: "POST /xmlrpc.php HTTP/1.0", upstream: "fastcgi://unix:/var/run/php5-fpm.sock:", host: "jayxon.com" 2015/07/10 08:44:19 [error] 2858#0: *13811 connect() to unix:/var/run/php5-fpm.sock failed (11: Resource temporarily unavailable) while connecting to upstream, client: 185.62.189.239, server: jayxon.com, request: "POST /xmlrpc.php HTTP/1.0", upstream: "fastcgi://unix:/var/run/php5-fpm.sock:", host: "jayxon.com" 2015/07/10 08:44:20 [error] 2858#0: *13813 connect() to unix:/var/run/php5-fpm.sock failed (11: Resource temporarily unavailable) while connecting to upstream, client: 185.62.189.239, server: jayxon.com, request: "POST /xmlrpc.php HTTP/1.0", upstream: "fastcgi://unix:/var/run/php5-fpm.sock:", host: "jayxon.com" 2015/07/10 08:44:20 [error] 2858#0: *13815 connect() to unix:/var/run/php5-fpm.sock failed (11: Resource temporarily unavailable) while connecting to upstream, client: 188.209.52.133, server: jayxon.com, request: "POST /xmlrpc.php HTTP/1.0", upstream: "fastcgi://unix:/var/run/php5-fpm.sock:", host: "jayxon.com" 2015/07/10 08:44:20 [error] 2858#0: *13817 connect() to unix:/var/run/php5-fpm.sock failed (11: Resource temporarily unavailable) while connecting to upstream, client: 188.209.52.133, server: jayxon.com, request: "POST /xmlrpc.php HTTP/1.0", upstream: "fastcgi://unix:/var/run/php5-fpm.sock:", host: "jayxon.com"
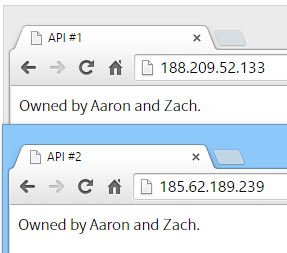
分析log发现大量重复POST请求xmlrpc.php,来自两个ip地址188.209.52.133和185.62.189.239,伪装成Google的爬虫。
185.62.189.239 - - [10/Jul/2015:08:48:23 +0000] "POST /xmlrpc.php HTTP/1.0" 499 0 "-" "Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html)" 188.209.52.133 - - [10/Jul/2015:08:48:23 +0000] "POST /xmlrpc.php HTTP/1.0" 499 0 "-" "Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html)" 185.62.189.239 - - [10/Jul/2015:08:48:23 +0000] "POST /xmlrpc.php HTTP/1.0" 499 0 "-" "Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html)" 188.209.52.133 - - [10/Jul/2015:08:48:23 +0000] "POST /xmlrpc.php HTTP/1.0" 499 0 "-" "Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html)" 188.209.52.133 - - [10/Jul/2015:08:48:24 +0000] "POST /xmlrpc.php HTTP/1.0" 499 0 "-" "Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html)" 185.62.189.239 - - [10/Jul/2015:08:48:24 +0000] "POST /xmlrpc.php HTTP/1.0" 499 0 "-" "Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html)" 185.62.189.239 - - [10/Jul/2015:08:48:24 +0000] "POST /xmlrpc.php HTTP/1.0" 499 0 "-" "Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html)" 185.62.189.239 - - [10/Jul/2015:08:48:24 +0000] "POST /xmlrpc.php HTTP/1.0" 499 0 "-" "Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html)" 188.209.52.133 - - [10/Jul/2015:08:48:24 +0000] "POST /xmlrpc.php HTTP/1.0" 499 0 "-" "Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html)" 185.62.189.239 - - [10/Jul/2015:08:48:25 +0000] "POST /xmlrpc.php HTTP/1.0" 499 0 "-" "Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html)" 185.62.189.239 - - [10/Jul/2015:08:48:25 +0000] "POST /xmlrpc.php HTTP/1.0" 499 0 "-" "Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html)" 188.209.52.133 - - [10/Jul/2015:08:48:25 +0000] "POST /xmlrpc.php HTTP/1.0" 499 0 "-" "Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html)"
访问这两个ip地址发现攻击者是Aaron和Zach。
抓取到Payload如下
POST /xmlrpc.php HTTP/1.0 Host: jayxon.com Content-type: text/xml Content-length: 263 User-agent: Mozilla/5.0 (compatible; Googlebot/2.1; http://www.google.com/bot.html) Connection: close <?xmlversion="1.0"?><methodCall><methodName>pingback.ping</methodName><params><param><value><string>http://panel.gamersolutions.net/</string></value></param><param><value><string>https://www.jayxon.com/thunder7-2-13/</string></value></param></params></methodCall>
看上去只是正常的Pingback,但实际上收到请求后WordPress会访问http://panel.gamersolutions.net/,也就是说攻击者在利用我的服务器来攻击http://panel.gamersolutions.net/(这个网站昨天还能打得开,现在就已经挂掉了)
临时解决办法是把xmlrpc.php文件重命名,反正这个文件没什么太大作用。
目前CPU占用降下来了,博客也恢复正常,但是攻击仍在持续攻击已停止。

也就两个 IP,索性防火墙里全部 drop 掉吧
WordPress 就不对这个做点限制什么的吗..
很嚣张啊,敢动你。
你让他等着,我去打他啊!
再次上来看看,迅雷依旧没有更新可下
J大现在作品有点少。
想下载大侠的Ashampoo Photo Commander 11,到处找不到,只能找到12,请问何处能下载到11?
我并没有做过你说的这个软件
不好意思……刚发现自己弄错了,打扰了!
他的目的是什么呀
大神太厉害了,请收我为徒吧!——来自一个做IC的小伙
这么嚣张,无聊的人真多啊
他们是在尝试爆破管理员密码,这个xmlprc文件有点Bug,想要通过xmlprc发表文章又必备不可,但是又会成为攻击的靶子。
你说的爆破密码是另外一个漏洞,当时这个只是利用我的网站攻击别人而已。
我都是专门新建了个sb.conf,把那些暴力破解/?author=1的IP都填进去,然后在ngnix.conf里填加个执行,经过两三个月的添加,现在安静多了,隔四五天才会有一次了
我的站前两天也是遇到这个情况了,
http://www.zzjiude.com